Listen to this article
Think about it. Once your phone is hacked, a complete stranger can go through your private contact list and your bank details, pretend they’re you, and do anything they want with your life. The potential personal and financial setbacks are so scary that it’s almost not worth having a smartphone.
But they’re so darn convenient! You can do almost anything with a smartphone. It’s like having a personal minicomputer in your pocket. We’ve gotten so used to accomplishing daily to-do list items without leaving the couch, the thought of driving to the bank to make a simple deposit seems ridiculous.
But what happens when our precious personal minicomputers are hacked? Is it the beginning of a long nightmare?
It doesn’t have to be. We’ll explain step-by-step exactly what to do if your phone has been hacked.
- How to Know if Your Phone Was Hacked
- My Phone Was Hacked. How Do I Fix It?
- How to Protect Your Phone From Getting Hacked Again
How to Know if Your Phone Was Hacked
First, what exactly is phone hacking? It’s when someone forces their way (digitally) into your phone. Once a cybercriminal accesses your phone, all the personal details inside your phone are exposed.
Worried about the newest data breaches? You can take control today.
Got a gut feeling that your phone has been hacked? Let’s go over some red flags that might prove your hunch.
Loses Its Charge Quickly
If you notice that the little battery indicator at the top of your phone screen drains more quickly than usual, it could be a sign that your phone has been hacked. Malicious apps and malware use a lot of battery power.
Or maybe your phone is just getting old? Could be. But either way, it’s not a good sign.
Runs Abnormally Slowly or Feels Hot
All smartphones run slowly occasionally. Maybe it’s just from a temporary network problem or maybe you have too many open apps and programs? Maybe. Maybe not.
If slow performance is due to hacker activity, it’s because when malware is running, it’s like having a second person using your phone and taking up all your processing power. So, if your phone is abnormally slow, or if it feels hot to the touch, it could mean that your phone is working overtime because it’s been hacked.
Strange Activity on Your Online Accounts
Big red flag here. If you see weird activity in your bank statement or social media accounts, it’s a possible sign that a hacker has hijacked your phone. Once they gain access, they can use your phone (virtually) to transfer data, make purchases, send messages or make phone calls and pretend they’re you. Yikes!
Unfamiliar Apps, Calls or Texts
Sometimes we forget which app we installed. Or even which text we sent to who. It happens. But typically, it doesn’t happen repeatedly.
If you notice frequent unfamiliar app, text or phone call activity, chances are your phone has been hacked. Hackers can potentially impersonate you to steal personal information from your loved ones. Be wary here. This can have widespread consequences.
It’s true that some of these indicators are just typical smartphone glitches. But be on the lookout—if you notice one or more of these red flags appear consistently, it likely means your phone has been hacked and it’s time to take action.

What's your risk of identity theft?
Take this quiz to assess your risk.
My Phone Was Hacked. How Do I Fix It?
Now that you’ve learned how to identify if someone hacked your phone, it’s time to make things right. Here are some easy steps for removing those cybercriminal activities from your phone and getting it back to normal.
1. To start, install and run security software on your phone.
Doing this will tell you which apps, calls or texts are risky and should be deleted. If you’re an iPhone user, you get a pass here because iPhones have built-in malware protection.
If you’re an Android user, Google’s Protect app is built into the Android operating system, and it’s free. It’s the least expensive way to find and remove Android phone viruses. Note: A third-party tool might offer a more secure option.
Here’s how to use Google Protect:
- Open the Google Play Store.
- Open the menu button by tapping on the profile icon in the top-right corner of your screen.

- Select Play Protect.
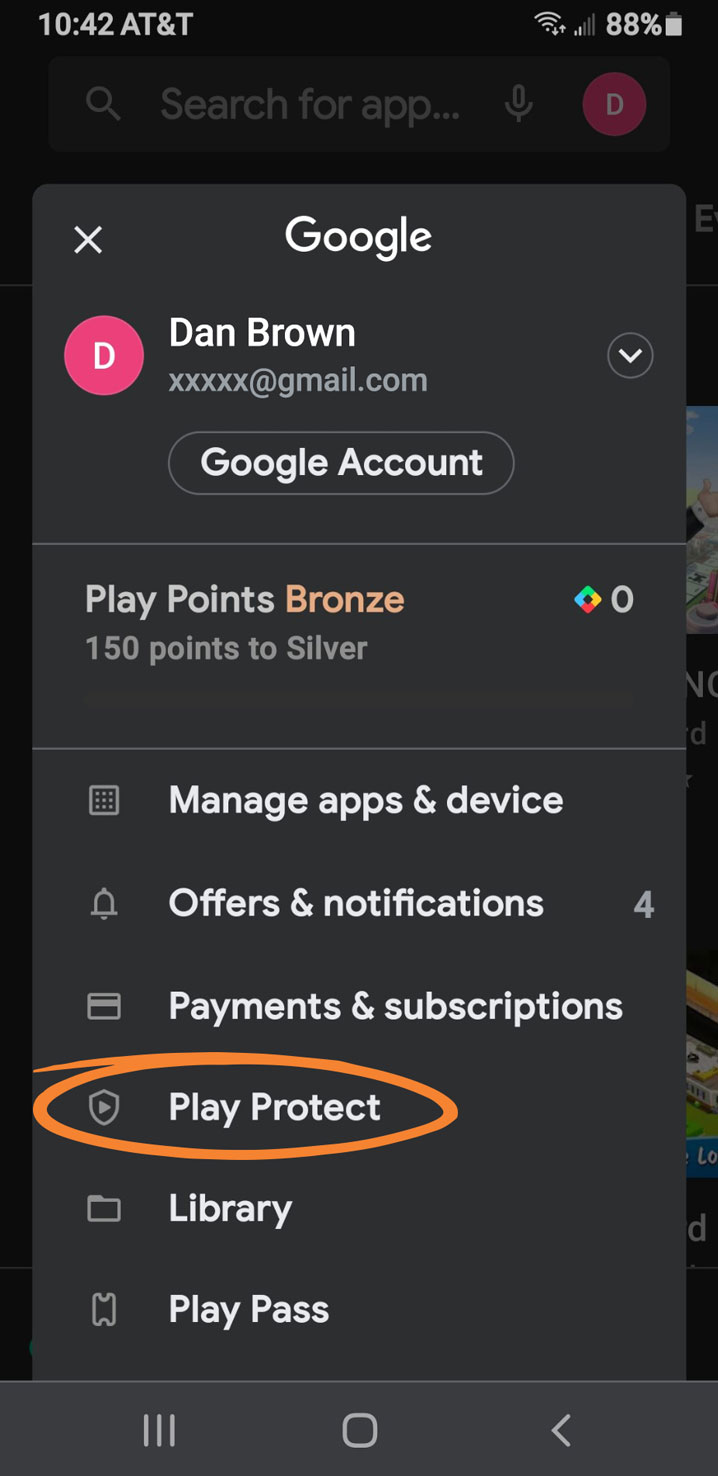
- Tap Scan. Your phone will check for Android malware.
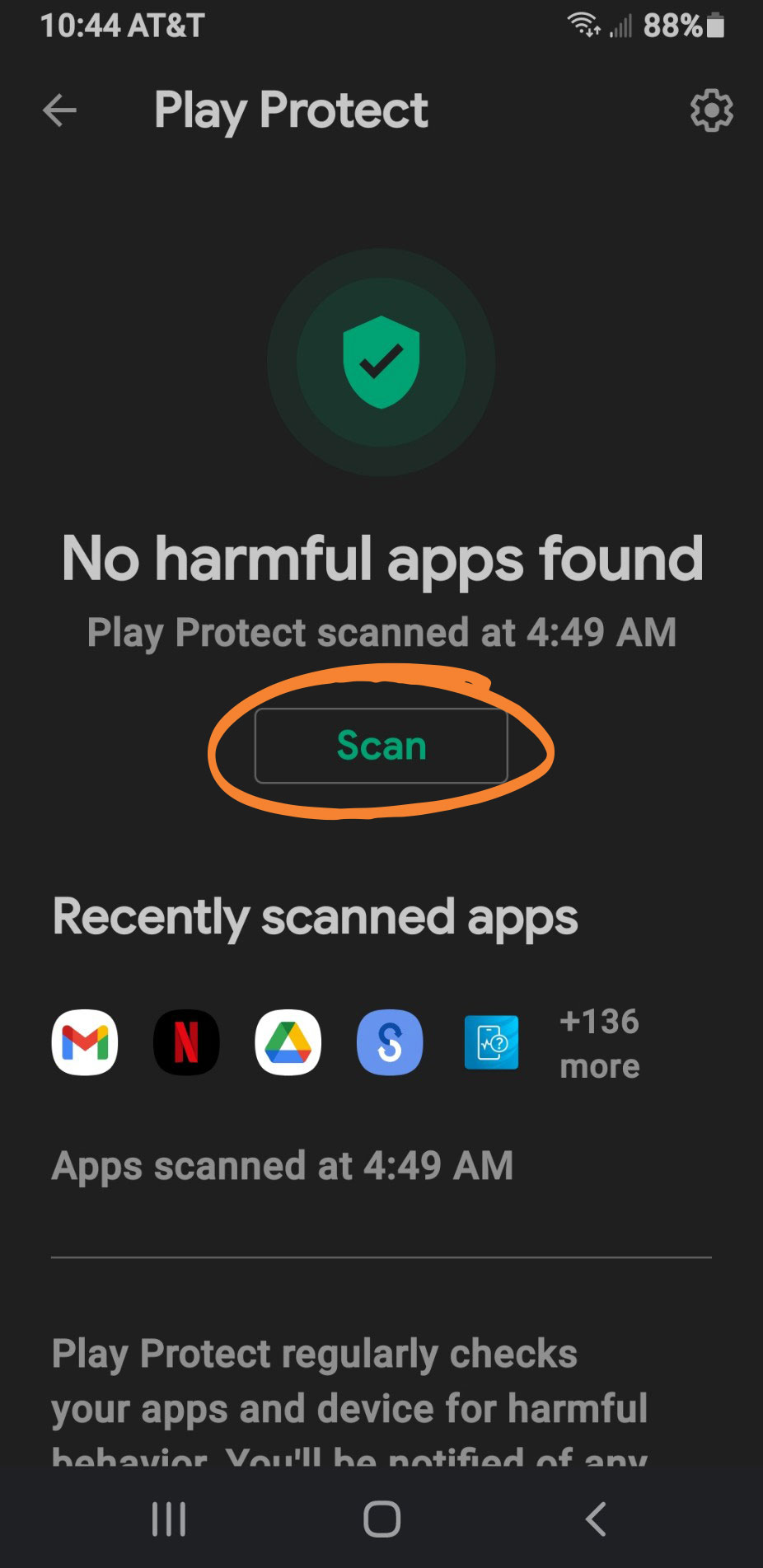
- If harmful app(s) are found, you’ll be prompted to remove them. Select Uninstall.
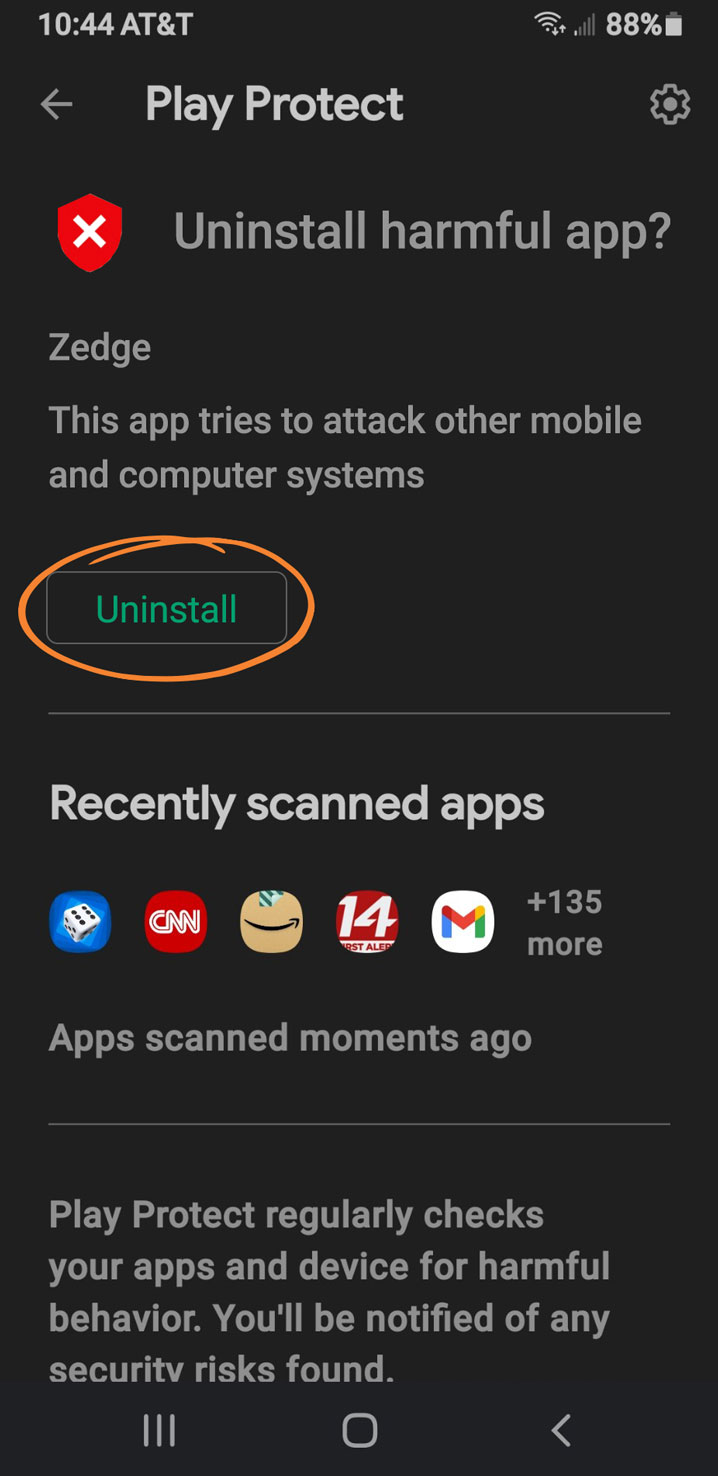
- After you’ve deleted the risks, run the Protect app again to make sure your phone is now risk-free.
Once you successfully remove the malware, take a look at identity theft protection from Zander, a RamseyTrusted provider. They offer proactive monitoring, so your phone never gets hacked again.
2. Next, check your bank accounts and your credit card statements.
Check to see if any unauthorized purchases have been made. If your accounts have been hacked, know that cleaning up an identity fraud situation could take years to handle on your own. We recommend identity theft protection from Zander. They’re RamseyTrusted and can assign a qualified person to clean up the mess for you.
3. If you still have issues, wiping and then restoring your phone is an option.
This step should be a last resort. But before you do this, make sure you have a recent backup of your photos, contacts and all other vital information, because you’re about to permanently remove them from your phone. A quick online search will lead you to instructions for wiping and restoring your phone.
Interested in learning more about identity theft?
Sign up to receive helpful guidance and tools.
How to Protect Your Phone From Getting Hacked Again
Phew! The hard part is over. Let’s make sure your phone never gets hacked again. We put together a list of easy tips to keep your phone safe.
Don’t Download Sketchy Software (Including Apps)
There are two simple ways to tell if you’re about to download sketchy software. The first way is to look at the domain name of the website you’re on (the domain name is in your browser’s address field toward the top of your screen). If you don’t see a recognizable domain name like microsoft.com or ibm.com, investigate further.
Next read the reviews. Internet reviewers are typically very up-front about their experiences online. If the review warnings sound legit, don’t download the software.
Always Keep Your Phone with You
This one’s easy. Physical access to your phone is the fastest way for hackers to do their thing. Once they have your phone, it only takes a day for them to break into it and hijack your contacts list, passwords, bank account details and anything else they consider valuable. Don’t make it easy for them—keep your phone with you at all times.
Always Use a Passcode Lock
Yes, it’s super annoying to enter a passcode every time you want to use your phone. But passcodes add a critical layer to preventing cybercriminal activity. And remember not to use any easy passcodes like your birthday or your street address—instead, think of a number that only you know about.
Avoid Public Charging Stations
Charging your phone at a public station might seem convenient at the time, but beware, hackers are lying in wait to pounce. They install malware into the charging station—just waiting for you to come along and innocently connect your phone.
Seems like a weird thing to do, right? Yes. But remember that lots of hackers make their living stealing people’s identities off of their phones and using stolen passwords to hack into bank accounts and steal money.
Always Enable Two-Factor Authorization
Okay. We admit it. Two-factor authorization (2FA) used to be a pain. The first step required you to remember your username and password and type it correctly. Then you had to retrieve a code from your phone, and again, remember it, and type it into the screen prompt correctly. Grrr.
But hold on, 2FA has gotten much easier. Biometrics like fingerprints and face ID have made it much simpler. What could be easier than shoving your face in front of your phone to prove it’s really you?
No more excuses. 2FA is well worth the effort and is now a simple way to add an extra layer of protection to your phone.
Protect Yourself From Cybercriminals
Don’t be an easy mark for criminal activity. There’s a smart way to proactively safeguard yourself and your loved ones from the nightmare of phone hacking and stolen identity.
Check out identity theft protection from RamseyTrusted provider Zander. They’ll monitor all your devices and notify you when/if they’re at risk and provide complete recovery services if needed.